When people think of cyberattacks, they often picture shadowy hackers breaking in from the outside. The reality is more unsettling. Increasingly, the biggest risks come from the inside. Employees, contractors, and trusted partners have access to sensitive systems and data, and when that trust is broken, whether intentionally or accidentally, the damage can be staggering.
The Numbers Tell the Story
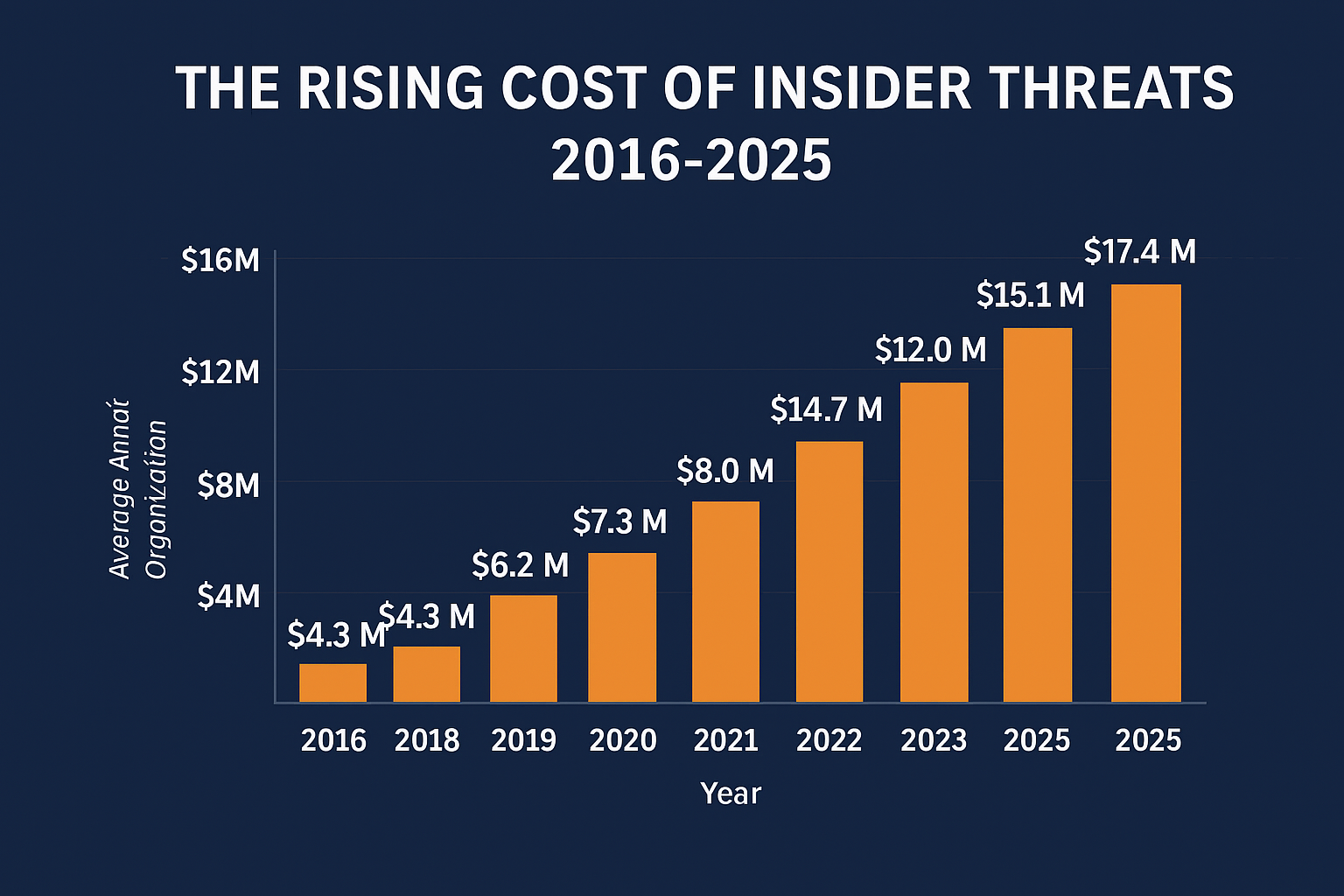
Insider threats are not a niche problem anymore. They are a global crisis. Over the past decade, the costs have skyrocketed.
| Year | Average Annual Cost per Organization | Average Number of Incidents | Avg Containment Time | % of Orgs Impacted |
| 2016 | $4.3 million | ~2,500 | ~70 days | ~60% |
| 2018 | $8.7 million | ~3,200 | ~74 days | ~65% |
| 2020 | $11.45 million | ~3,800 | ~77 days | ~70% |
| 2023 | $15.38 million | ~4,700 | 86 days | 80% |
| 2025 | $17.4 million | ~13.5 per org | 81 days | 83% |
Key takeaways:
- Costs have quadrupled since 2016.
- Incidents are more frequent, rising from ~2,500 in 2016 to ~13.5 per organization in 2025.
- Containment times remain stubbornly high, averaging 70–86 days across the decade.
- The percentage of organizations impacted has climbed steadily, reaching 83 percent in 2025.
Why Insider Threats Are Rising
Several forces are driving this surge:
- Remote and hybrid work: Employees continue to access sensitive systems from home networks and personal devices, which expands the attack surface and makes monitoring harder (Verizon DBIR, 2025).
- Economic pressures: Layoffs, job dissatisfaction, and financial stress in 2025 have pushed more insiders toward malicious activity or negligence (Forrester, 2025).
- Access mismanagement: Many organizations still grant excessive privileges or fail to revoke access quickly when employees leave, creating opportunities for abuse (Gartner, 2025).
- Sophisticated tactics: Threat actors increasingly recruit insiders or exploit them through social engineering, making insider risk part of broader attack campaigns (MITRE, 2025).
What Organizations Are Doing About It
The good news is that organizations are not ignoring the problem. Many are investing heavily in insider threat programs. Ponemon found that 81 percent of organizations now have dedicated insider risk management strategies, and budgets for insider risk have nearly doubled since 2023. Common strategies include:
| Mitigation Strategy | Description |
| User and Entity Behavior Analytics (UEBA) | AI driven monitoring that flags unusual activity patterns. |
| Zero Trust Architecture | Limiting access based on continuous verification rather than blanket trust. |
| Privileged Access Management (PAM) | Restricting and auditing high level accounts to prevent abuse. |
| Employee Awareness Training | Teaching staff to recognize risks and avoid negligent behavior. |
| Data Loss Prevention (DLP) | Blocking unauthorized transfers of sensitive files. |
| Cross‑functional Insider Threat Teams | Combining HR, legal, and security expertise to detect and respond quickly. |
Despite these efforts, the Ponemon Institute found that the average time to contain an insider incident in 2025 is still 81 days, which is far too long when sensitive data is at stake.
The Human Factor
What makes insider threats uniquely challenging is the human element. Unlike malware or phishing emails, insiders are trusted by default. They know the systems, the processes, and often the weaknesses. That is why insider threats are not just a technical problem but a cultural one. In 2025, organizations need to foster transparency, accountability, and trust while still enforcing strict controls.
The Bottom Line
From 2016 to 2025, insider threats have grown from a costly nuisance into a defining cybersecurity challenge. Costs have quadrupled, incidents are more frequent, and containment times remain stubbornly long. Organizations are responding with advanced tools and strategies, but the problem is deeply human and will not be solved by technology alone. As remote work, economic stress, and evolving tactics continue to reshape the landscape, insider threats will remain one of the most pressing cybersecurity challenges of our time.
Sources
- Ponemon Institute. 2016 Cost of Insider Threats Report. Link
- Ponemon Institute. 2020 Cost of Insider Threats Global Report. Link
- Ponemon Institute. 2023 Cost of Insider Threats Global Report. Link
- Ponemon Institute. 2025 Cost of Insider Threats Global Report. Link
- DeepStrike. Insider Threat Statistics 2025. Link
- Insider Risk Research. The Hidden Enemy: 2025 Insider Threat Intelligence Report. Link
- Verizon. 2025 Data Breach Investigations Report. Link
- Forrester. The State of Insider Threats 2025. Link
- Gartner. Zero Trust and Insider Risk Guidance 2025. Link
- MITRE. Insider Threat Knowledge Base 2025. Link